Education and Training Materials:
Technology always comes with the cost of training the people who use and deploy it. Nothing is ever simple. The first time you drove a car took some degree of training and as you drove, you gained experience. Now, you probably never think twice about how EASY it seems to be! But for the beginner, it took some time to learn about steering, brake and accelerator pedals, gearshift, and gauges, and traffic laws, and the list goes on. The same can be expected with any facet of the Amateur Radio hobby - everything comes at the cost of investing some time into learning how things work and how to operate them most efficiently. It always feels overwhelming, at first, but becomes easy or natural as we get more accustomed to it.
So let's start by covering your basic education in What is Packet Radio? And then we will build from there, through the AX.25 Protocol, Link-Layer Protocols, Internet Protocol (IP), Transport Control Protocol (TCP), User Datagram Protocol (UDP), File Transfer Protocol (FTP), and Simple Mail Transport Protocol (SMTP). We will also cover Address Resolution Protocol (ARP) and Domain Name Service (DNS). All of which will depend upon a good understanding of the OSI 7 Layer Model, a convienient way to keep our mind focused on where we are within the structure of data communications.
And later, we will get into routing and how the IPIP Encapsulation protocol is used to route AMPRnet packets across the Public Internet, allowing us to connect every Hamgate gateway router with every other on the Planet!
What is Packet Radio?
Rather than duplicate the fine writings of Greg Jones, WD5IVD (sk), I will point you
to his material on the TAPR website.
A good book about Packet Radio is available through TAPR (Tucson Amateur Packet Radio) called Packet Radio. What? Why? How?
Online referances that explain the basics of Packet Radio are available on the TAPR.org website at: https://www.tapr.org/pr_intro.html
More Packet related information can be found at: https://www.tapr.org/packetradio.html
Too many hops through DIGIPEATERS will seriously kill your effective throughput.
Avoid having more than one hop if at all possible. Here is a (rather technical) study done by
Tom Clark W3IWI, submitted to the 1986 Digital Communications Conference called
The Problem With Digipeaters - By: Tom Clark, W3IWI - 16 December 1986
The AX.25 Protocol (Protocol-93):
AX.25 has a Protocol ID (PID) in its packet header indicating what kind of data is contained inside the "payload".
Plain text keyboard-to-keyboard AX.25 will set the PID to 0xF0, but for AX.25 carrying Internet Protocol (IP), the
PID will be set to 0xCC. As an aside, the PID is set to 0x.. for TexNet and 0x.. for NetROM.
Link Layer (L2) Protocols:
Link Layer protocols are those that are just above the Physical Layer. These are the protocols that run over the top of wires, or coax, or RF. The Ethernet 802.3 is a Link Layer protocol and defines the Frames that ride over Ethernet coax and twisted-pair cable. These use the MAC (Machine Address) address of the Ethernet card as the identity of each computer on the network. In Packet Radio the AX.25 protocol is a Link Layer protocol that rides over Radio, and we use our Callsigns to identify the Hardware address on each end of a link.
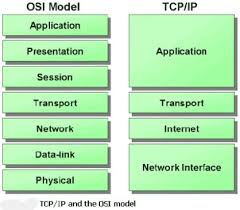
The 7-Layer OSI Model:
The Seven Layer OSI Model compartmentalizes the logical components of the communications protocols, whether they be X.25, AX.25, ARCnet, IPX, TCP/IP, or other. The seven layers are as follows:
Layer 7 --- Application - The software that generates the traffic (Telnet/Finger/SMTP/SNMP/HTTP)
Layer 6 --- Presentation - Character set (ASCII/EBCDC), font size, color, screen addressing, cursor positioning
Layer 5 --- Session - Login (UID/PW)
----------------------------------------------------------------------
Layer 4 --- Network - End-to-End packets (TCP/UDP/ICMP)
Layer 3 --- Packet - Point-to-Point packets (IP)
Layer 2 --- Link - Basic framing, clocking, addressing, and checksum (802.3, AX.25)
Layer 1 --- Physical - Wire, cable, phoneline, Radio, fiberoptics
The 7 Layer Model has just that, SEVEN layers. But in the TCP/IP world they have come to consider layers 5 through 7 as the Application layer and don't make any distinction regarding the functions of Session and Presentation, balling them together as an integral part of the Application. This is all true until you need to troubleshoot why an end user is getting Chineese on their screen instead of English. THEN you need to understand the end-to-end handshake that goes on within protocols like "Telnet" that negotiate such things ("Options Negotiation").
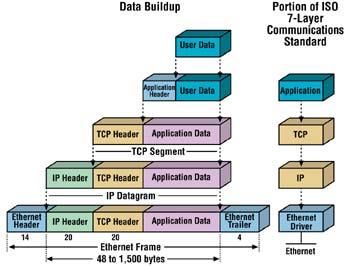
How the Layers are Encapsulated into one another:
XXXXXxxxx......
In the image below, we see how data travels from the Application on one Host, down through
the OSI stack, put into Ethernet frames, then sent across a Physical medium to another Host
on the same "collision doamin". Then back up through the OSI stack to the Application on the
destination Host computer.
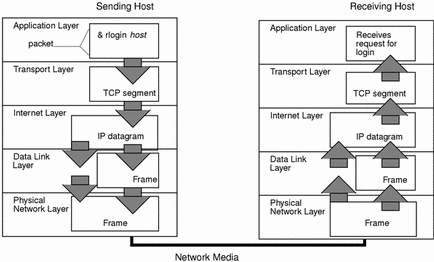
We can insert additional OSI stacks along the circuit between the two Hosts, but these stacks will ONLY go up as high as Layer-4 Transport, which is where ROUTING decisions are made. Then back down the stack to the desired interface/link that sends the traffic on toward its desired destination. There can be as many intermediate nodes/stacks in between the two Hosts as maybe needed. This is how Networks are built.
Internet Protocol (IP):
Internet Protocol (IP) is a Point-to-Point protocol that ONLY connects two machines within the same collision domain. That is, it can connect two machines on the same Ethernet cable, or on opposite ends of a T1 data circuit, or two Packet Radio stations on the same Frequency within range of one another. IP is NOT routed!. It is used to establish a dependable connection between two machines/computers and then carries *other* protocols on TOP of the IP. The other protocols may be ICMP, TCP, UDP, etc.
A large number of so-called Network Professionals have never wrapped their heads around this, and it causes much grief in the I.T. crowd from time to time. IP is point-to-point in the same collision domain and is NOT routed. TCP is what gets routed as it connects endpoints across a network of routers forming the Transmission path (Hmmm? Is that why it's called "Transmission Control Protocol"?).
Address Resolution Protocol (ARP):
Our computers don't really talk to one another via their IP addresses. They actually talk to one another via their Hardware or MAC address. This is the hard-coded serial number coded within every Ethernet board. And in the case of Packet Radio, we use our Callsign as the Hardware Address (i.e. WB8TKL-3) on our TNC's.
As we covered earlier, the AX.25 protocol is a Link Layer protocol and is ONLY used to go point-to-point between stations. This is the same with an Ethernet, that ONLY goes between computers point-to-point. This is called the collision domain where all computers within the collision domain are DIRECTLY able to talk to one another without going through a Router.
And here is how ARP works: When a computer needs to talk to another computer, it looks up the destination address (via DNS) and then references the Routing Table to determine the Interface to use to send the Packet out on. But as we covered earlier, computers don't really talk IP to IP, they talk MAC to MAC. So we need some mechanism to "resolve" the IP addresses to the MAC addresses of the computers involved.
Enter Address Resolution Protocol
The sending computer first sends out an ARP Request - Who Has querry to what is known as the Broadcast Address. Every computer on the collision domain listens to this Broadcast Address. The recieving computer hears the "Who Has" request and sees that the querry is for their IP address, so it responds with an ARP packet that contains their MAC address and their IP address. The Sending computer now writes that information into its ARP Table. This data will be stored in the ARP Table for only 5 or 10 minutes, and will be updated periodically if the two computers remain in communication with one another.
Now that the Sending computer knows the MAC address of the Destination computer, it can then send an Ethernet Frame (or an AX.25 frame) to the Destination. Contained on top of that Frame will be the IP Packet.
Internet Control Message Protocol (Protocol-1):
The Internet Control Message Protocol (ICMP) is part of the Internet Protocol Suite, as defined in RFC 792. ICMP messages are typically used for diagnostic or control purposes and may be used to generate responses to errors in IP operations (as specified in RFC 1122). ICMP errors are directed back toward the source IP address of the originating packet. It is important to *NOT* block ICMP in your firewalls as ICMP is a necessary compenent of other networking protocols (many I.T. folk block ICMP because they wrongly believe that ICMP does harm).
ICMP is most well known for its use in the Ping and Traceroute tools. ICMP is the underlying protocol that these tools use in performing their desired functions. ICMP is also used in determining the maximum (or minimum) Packet size or Maximum Transmission Unit (MTU) that an end-to-end connection can support. Sometimes intermediate links between routers can only handle smaller MTU sizes, which would otherwise make a larger MTU sized packet become blocked and traffic cannot flow through. A feature of ICMP is in its use in PMTUD.
Path MTU Discovery (PMTUD) is a standardized technique in computer networking for determining the maximum transmission unit (MTU) size on the network path between two Internet Protocol (IP) hosts, usually with the goal of avoiding IP fragmentation. PMTUD was originally intended for routers in Internet Protocol Version 4 (IPv4). However, all modern operating systems use it on endpoints.
For example, every device (such as an intermediate router) forwarding an IP datagram first decrements the time to live (TTL) field in the IP header by one. If the resulting TTL is 0, the packet is discarded and an ICMP Time To Live exceeded in transit message is sent to the datagram's source address. These give the feedback needed for Traceroute and Ping tests.
Although ICMP messages are contained within standard IP packets, ICMP messages are usually processed as a special case, distinguished from normal IP processing, rather than processed as a normal sub-protocol of IP. In many cases, it is necessary to inspect the contents of the ICMP message and deliver the appropriate error message to the application responsible for transmission of the IP packet that prompted the sending of the ICMP message. Typical ICMP types are: Echo Request, Echo Reply, Router Advertisement, Router Solicitation, Time Exceeded and Destination Unreachable.
Many commonly used network utilities are based on ICMP messages. The traceroute command can be implemented by transmitting IP datagrams with specially set IP TTL header fields, and looking for ICMP Time to live exceeded in transit and "Destination unreachable" messages generated in response. The related ping utility is implemented using the ICMP "Echo request" and "Echo reply" messages.
Transport Control Protocol (TCP) (Protocol-6):
User Datagram Protocol (UDP) (Protocol-17):
User Datagram Protocol (UDP) is an unconnected protocol. Instead of establishing a "connection", UDP mearly sends the Datagrams on their way with no guarentee of delivery nor any handshake that Datagrams arrived in the correct order, or arrived at all! UDP Datagrams are also limited to only 512 bytes, so they are relatively small. The advantage of UDP is that there is no time or resources wasted setting up a connection, like there is with TCP. There are never any "hung" connections since there was no connection to begin with.
UDP serves very nicely when *speed* is necessary - particularly on brief transactions such as when querrying a Domain Name Server or getting an accurate date/time in the Network Time Protocol (NTP). UDP allows us to get in and get out very quickly.
File Transfer Protocol (FTP):
Simple Mail Transport Protocol (SMTP):
SMTP is a Peer-to-Peer protocol. When email is to be sent to a particular destination, the two endpoint computers link up using TCP (covered earlier). SMTP rides over the top of TCP, and is a human-readable protocol, just like FTP was (covered earlier). The general handshake is for the two endpoints to announce who they are to one another, confirm that the recipient has an email account on the desination server, exchange the email Header information followed by the message content. An exchange occurs at the end of the exchange to confirm that the transaction is complete, and as is in all things UNIX/Linux an entry is made into the Log on both computers confirming the transaction.
Only then is the TCP connection between the two end points torn down.
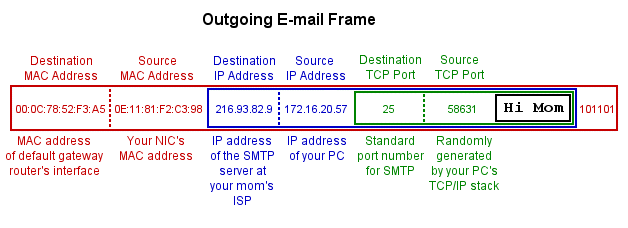 As you can see, SMPT is part of the Application Layer carried atop TCP, which goes Peer-to-Peer.
Be clear that IP only goes Point-to-Point (within the same collision domain) and does NOT ever get
routed! Only TCP is routed across the network.
As you can see, SMPT is part of the Application Layer carried atop TCP, which goes Peer-to-Peer.
Be clear that IP only goes Point-to-Point (within the same collision domain) and does NOT ever get
routed! Only TCP is routed across the network.
Routing Tables:
Routing tables are refered to each and every time a Packet needs to be transmitted from a computer or router. The Destination address (TCP/UDP address) is passed to the routing table to determine the best route to send out said Packet. The order in which we scan the Route Table is Most specific to Least Specific. That is, we first look for any 32-bit addresses that match our desirect Destination, if no match look for a 31-bit, and so on. In many cases we simply fail to find a "specific" route and fall through to what is called the
Not everywhere are we as Hams able to get from Point-A to Point-B without the help of the Internet. Sometimes we just don't have the resources to link everything together via Radio. So we have a special protocol called IPIP Encapsulation which allows us to take Packets that have Source and Destination addresses in the AMPRnet (44.0.0.0/8) and place them *inside* the typical Packets that we send across the public Internet. This is not unlike placing a letter inside an envelope (encapsulated), and then placing that envelope inside yet another envelope with a new set of TO and FROM addresses on it. Once the outside envelope reaches its destination, it is then opened (de-encapsulated) and the internal envelope's addresses are then used to route the letter to its final destination, in this case, within the AMPRnet.
IPIP Encapsulation (Protocol-4):
This is IPIP Encapsulation (Protocol-4) and we use this extensively inside our "Hamgate" routers. A special Routing Table called the ENCAP.TXT route table is used to determine the routes to all the Subnets that all the Hamgates worldwide are routing. Hear is a sample of what that table looks like:
route addprivate 44.135.49/24 encap 173.0.202.7
route addprivate 44.102.135/24 encap 173.14.57.181 <------- Hamgate.Muskegon.AMPR.org Subnet 44.102.135.0/24
route addprivate 44.4.2.152/32 encap 173.167.109.217
route addprivate 44.4.2.153/32 encap 173.167.109.217
route addprivate 44.16.2.32/27 encap 173.60.166.190
route addprivate 44.64.28/24 encap 173.63.170.47
route addprivate 44.135.84/24 encap 184.175.46.166
route addprivate 44.174.43/24 encap 189.42.190.50
route addprivate 44.2.8.180/30 encap 192.147.172.252
So in the route line highlighted above, any traffic destined for the 44.102.135/24 subnet in Muskegon, Michigan, will be encapsulated and then sent to the PUBLIC IP address of 173.14.57.181 - the address of the Hamgate's Internet connection. Hamgate.Muskegon then de-encapsulateds the packet, extracting the original packet destined for someone in the 44.102.135 subnet. The Hamgate then passes that Packet through its regular route table to determine how best to deliver it, generally by some RF path.
In the image, below, the "Original Endpoints" would be the 44-net addresses. And the "Tunnel Endpoints" would be the Public Internet IP addresses of the the two Hamgate gateways involved.
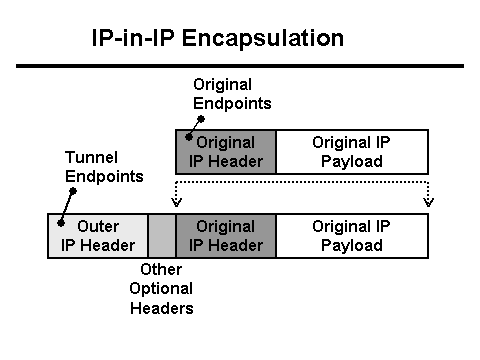
For this to work correctly, every Hamgate gateway *should* keep their ENCAP.TXT route table up to date as Public Internet IP addresses tend to change, as do subnet assignments.
Domain Name Service (DNS):



